Ethical Hacking vs. Hacking
In the world of cybersecurity, the terms "hacking" and "ethical hacking" often coexist, yet they represent two vastly different approaches and ethical stances. The distinction between the two is crucial for understanding their respective roles, motivations, and implications. While both involve penetrating computer systems, their intents, methodologies, and outcomes differ significantly.
According to findings from a Fortune Business Insight report, the global cybersecurity sector is poised for substantial expansion, with projections indicating a rise from $172.32 billion in 2023 to an impressive $424.97 billion by 2030. This expansion demonstrates a strong compound annual growth rate (CAGR) of 13.8%. This article aims to shed light on these disparities and emphasize the importance of ethical conduct in the realm of hacking.
Exploring Ethical Hacking versus Hacking
Ethical hacking and hacking are two terms often used interchangeably, but they refer to distinct activities with different motivations and ethical considerations.
Ethical hacking involves the use of hacking techniques to identify vulnerabilities in computer systems, networks, or applications with the explicit permission of the system owners. Ethical hackers, also known as penetration testers or white-hat hackers, employ their skills to assess the security posture of an organization and help improve its defences. Their activities are conducted within legal and ethical boundaries, focusing on uncovering weaknesses that malicious hackers could exploit. Ethical hacking serves as a proactive measure to strengthen cybersecurity by preemptively addressing potential threats and fortifying digital infrastructure against cyber attacks.
On the other hand, hacking refers to the unauthorized intrusion into computer systems, networks, or devices with malicious intent. Hackers, often termed black-hat hackers or crackers, exploit security flaws to gain unauthorized access, steal sensitive information, disrupt operations, or cause harm to individuals or organizations. Hacking activities are illegal and unethical, violating privacy rights and compromising the integrity and confidentiality of data. Unlike ethical hacking, hacking is driven by personal gain, ideological motives, or malicious intent, posing significant risks to individuals, businesses, and society at large.
Refer:
- Who exactly is a hacker?
- What really is Hacking?
- Difference between Cyber Security & Ethical Hacking
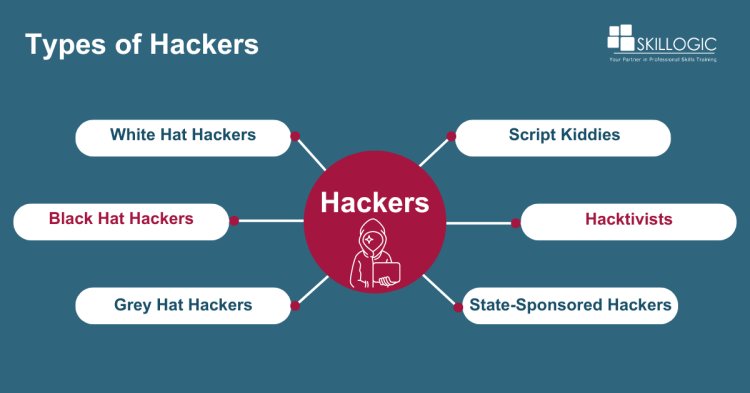
Types of Hackers
Hackers can be categorized into several types based on their motives, techniques, and activities. Here are some common classifications:
- White Hat Hackers: Also known as ethical hackers, these individuals use their hacking skills for legal and beneficial purposes. They often work as security professionals to identify vulnerabilities in systems and networks to help organizations improve their security.
- Black Hat Hackers: These hackers engage in illegal activities for personal gain, malicious intent, or financial profit. They are responsible for activities such as stealing data, spreading malware, conducting cyber espionage, and launching cyber-attacks.
- Grey Hat Hackers: Grey hat hackers operate between white hat and black hat hackers. They may violate laws or ethical standards to uncover vulnerabilities in systems but may not necessarily have malicious intentions. However, their actions can still have legal consequences.
- Script Kiddies: These are typically amateur hackers who lack deep technical knowledge but use readily available hacking tools and scripts to launch attacks. They often don't understand the intricacies of the attacks they execute and may not have clear motives beyond causing mischief or gaining notoriety.
- Hacktivists: Hacktivists are individuals who utilize their hacking abilities to advocate for social or political purposes. They may target government agencies, corporations, or organizations they perceive as unjust or oppressive, often to raise awareness or protest.
- State-Sponsored Hackers: Also known as Advanced Persistent Threat (APT) groups, these hackers are sponsored by governments to conduct cyber-espionage, sabotage, or influence operations against other nations, corporations, or individuals. They have significant resources and sophisticated techniques at their disposal.
Distinguishing Ethical Hacking from Hacking
Ethical hacking and hacking are two terms that refer to activities related to computer security, but they have distinct differences in their intent, legality, and ethical considerations:
Intent:
- Hacking: Hacking typically refers to gaining unauthorized access to computer systems or networks for malicious purposes. This can include stealing sensitive information, disrupting services, or causing damage to the system.
- Ethical Hacking: Ethical hacking, on the other hand, involves using hacking techniques to identify vulnerabilities and weaknesses in computer systems or networks with the permission of the owner. The goal is to improve security by fixing these vulnerabilities before malicious hackers can exploit them.
Legality:
- Hacking: Hacking is generally illegal and is considered a criminal activity in most jurisdictions. Unauthorized access to computer systems or networks is a violation of various laws, including the Computer Fraud and Abuse Act in the United States.
- Ethical Hacking: Engaging in ethical hacking is permissible when undertaken with appropriate authorization. Ethical hackers typically work under a legal contract, such as a penetration testing agreement, which grants them permission to test the security of a system or network.
Ethical Considerations:
- Hacking: Hacking disregards ethical considerations and often involves exploiting vulnerabilities for personal gain or to cause harm to others.
- Ethical Hacking: Ethical hackers adhere to a strict code of ethics and conduct. They respect the privacy and confidentiality of data, and their actions are aimed at improving security rather than causing harm.
Outcome:
- Hacking: The outcome of hacking is usually detrimental, leading to data breaches, financial losses, or other negative consequences for the victims.
- Ethical Hacking: The outcome of ethical hacking is positive, as it helps organizations identify and fix security vulnerabilities before they can be exploited by malicious actors. This ultimately enhances the organization's overall security stance.
Purpose:
- Hacking: The purpose of hacking is often to steal sensitive information, compromise systems for financial gain, disrupt services, or cause harm to individuals or organizations.
- Ethical Hacking: The purpose of ethical hacking is to assess the security posture of systems and networks, identify vulnerabilities, and provide recommendations for improving security. Ethical hackers help organizations strengthen their defenses against malicious attacks.
Methodology:
- Hacking: Hackers may use various techniques such as exploiting software vulnerabilities, social engineering, phishing, malware, and brute force attacks to gain unauthorized access to systems or networks.
- Ethical Hacking: Ethical hackers use similar techniques as malicious hackers but with the intention of uncovering and addressing security weaknesses. They employ penetration testing methodologies, vulnerability assessment tools, and best practices to simulate real-world attacks and assess security controls
Refer:
Ethical hacking involves authorized and legal penetration testing to identify vulnerabilities in systems with the goal of enhancing security. It operates within ethical boundaries, with the intention of improving cybersecurity measures. Conversely, hacking refers to unauthorized access to systems for malicious purposes, often leading to breaches, data theft, and other illegal activities. The key distinction lies in the intent and legality, with ethical hacking contributing to proactive defence against cyber threats, while hacking poses significant risks to individuals, organizations, and society as a whole.
Prospective individuals have the opportunity to join SKILLOGIC Institute, a globally renowned training provider acclaimed for its specialized certification programs in Project Management, Quality Management, Cybersecurity, Software Development, and Business Analytics. With a proven track record spanning more than a decade, SKILLOGIC® distinguishes itself as a prominent figure in the industry, serving a diverse international student community exceeding 100+ learners. With an extensive offering of over 25 accreditations and partnerships, and supported by a dedicated team of over 100 experienced instructors, SKILLOGIC® provides a comprehensive learning experience for those aspiring to enhance their skills and progress in their careers.

0
238