Cyber security vs. Information Security: What’s the Difference?
In today’s digital age, protecting data is more crucial than ever. As businesses, governments, and individuals increasingly rely on technology, ensuring sensitive information is secure has become a top priority. However, the terms "cyber security" and "information security" are often misunderstood or used interchangeably. While both play significant roles in data protection, they focus on different areas. This article will explore the differences and overlaps between cyber security and information security, helping you gain a clearer understanding of each. Whether you're considering a cyber security course or looking to deepen your knowledge, this guide will clarify the key concepts.
What Is Cyber Security?
Cyber security is the practice of protecting digital systems, networks, and devices from cyberattacks. Its primary goal is to defend against external threats, including hackers, malware, ransomware, and phishing attempts. In essence, cyber security focuses on safeguarding data and systems from unauthorized access or damage in the digital realm.
Key Components of Cyber Security:
- Network Security: Protects an organization’s network from both internal and external intrusions.
- Cloud Security: Secures data stored in the cloud, preventing breaches and mitigating vulnerabilities.
- Application Security: Ensures that software applications are free from security loopholes that could be exploited.
- Incident Response and Recovery: Involves responding to cyber security breaches and working to recover affected systems and data.
Together, these components create a comprehensive cyber security strategy designed to reduce the risk of cyberattacks and data breaches. As the world becomes more connected, cyber security training institute is increasingly important for individuals and businesses alike to understand and manage the evolving threat landscape.
Example Scenarios in Cyber Security:
- Preventing Ransomware Attacks: Cyber security strategies employ tools like antivirus software, encryption, and network monitoring to prevent ransomware from seizing control of systems.
- Securing Digital Infrastructure: Implementing firewalls, multi-factor authentication, and intrusion detection systems helps protect a company’s network and servers from cyber threats.
As the demand for digital protection grows, enrolling in a cyber security course can be an excellent way to equip yourself with the necessary skills to safeguard against these threats. Cyber security training provides individuals with hands-on experience in identifying and preventing cyberattacks.
cyber security is a vital component of today’s digital defense strategies. By focusing on protecting systems and data from external attacks, cyber security plays a critical role in keeping both individuals and organizations safe. Whether you're looking to pursue a cyber security course or simply want to enhance your understanding of digital protection, investing in cyber security training is a proactive step toward a more secure future.
Refer these articles:
- Top Cybersecurity Threats in 2024: What You Need to Know
- How to Prevent Phishing Attacks: Best Practices for 2024
- Top 7 Cybersecurity Certifications to Boost Your Career
What Is Information Security?
Information Security (often called InfoSec) is broader than cyber security. It focuses on protecting all forms of information—whether physical or digital. The primary goal of InfoSec is to ensure the confidentiality, integrity, and availability (CIA triad) of data, meaning that information remains secure, accurate, and accessible only to authorized individuals.
Key Components of Information Security:
- Physical Security: Protecting tangible assets like paper documents, hardware, and servers from unauthorized access or damage.
- Access Control and Encryption: Ensuring only authorized personnel can access sensitive data, whether through digital encryption or physical locks.
- Policies and Procedures: Establishing guidelines for how information is handled, accessed, and shared to ensure consistent protection.
Unlike Cyber Security, which is primarily concerned with external digital threats, information security encompasses broader controls that protect both physical and digital information from all types of cyber threats.
Example Scenarios in Information Security:
- Protecting Printed Documents: Storing sensitive documents in locked cabinets and ensuring only authorized individuals have access.
- Database Integrity and Backups: Implementing robust backup systems and access controls to ensure the integrity of a company's data.
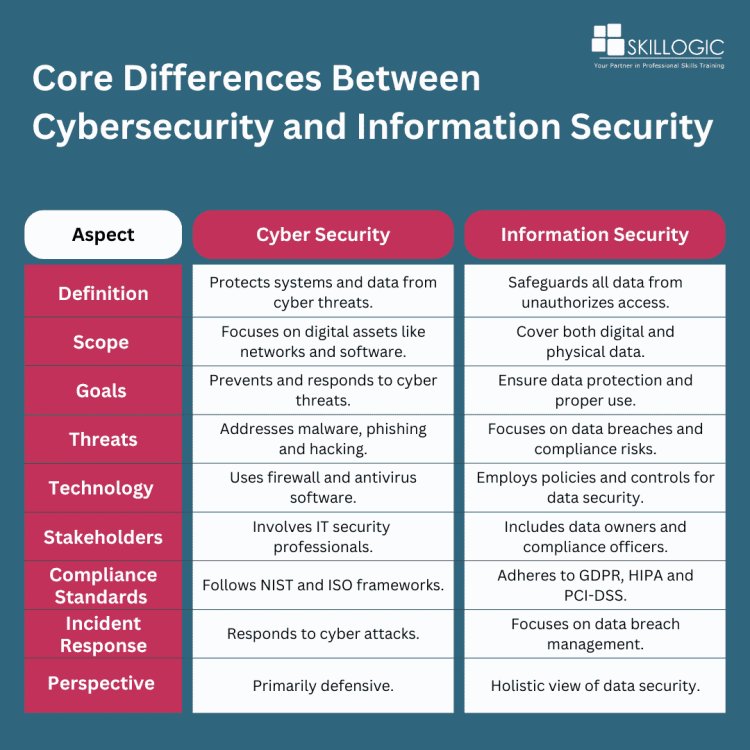
Core Differences Between Cyber Security and Information Security
Cybersecurity is primarily concerned with protecting computer systems, networks, and data from cyber threats and attacks. This includes defending against various forms of malicious activity that could compromise the integrity and availability of digital assets.
Information Security, on the other hand, focuses on safeguarding data itself, regardless of its format. This means protecting data from unauthorized access and disclosure, ensuring that sensitive information remains confidential and secure.
Scope
- The scope of cybersecurity is largely digital, dealing with assets such as hardware, software, networks, and the internet. It focuses on the protection of systems and networks from cyber threats that can affect digital environments.
- In contrast, information security has a broader scope that encompasses both digital and physical data. It emphasizes the principles of confidentiality, integrity, and availability of information, regardless of whether that data is in digital form or stored in physical formats.
Goals
- The primary goal of cybersecurity is to prevent, detect, and respond to various cyber threats and vulnerabilities. This involves implementing defensive measures to protect systems from attacks and breaches.
- Information security aims to safeguard data from unauthorized access and ensure its proper use. This includes maintaining the security of information against theft, loss, or unauthorized sharing, thus preserving its integrity and confidentiality.
Threats
- Cybersecurity addresses a range of threats specific to the digital realm, including malware, phishing attacks, hacking attempts, and denial-of-service (DoS) attacks. It focuses on the tactics and techniques employed by cybercriminals to exploit vulnerabilities in systems.
- Conversely, information security is concerned with risks related to data breaches, insider threats, data loss, and compliance violations. It looks at how data can be compromised, whether through external attacks or internal mishaps, and aims to mitigate these risks.
Technology
- In the realm of cybersecurity, the use of technology is vital. This includes implementing tools and practices such as firewalls, intrusion detection systems, antivirus software, and encryption to protect digital assets and systems.
- Information security relies on policies, procedures, and controls designed to protect data. This includes implementing access controls, encryption techniques, and data classification methods to ensure that data is handled securely and appropriately.
Stakeholders
- Cybersecurity typically involves IT security professionals, network administrators, and cybersecurity analysts who are focused on implementing technical measures to protect systems and networks.
- Information security, on the other hand, includes a broader range of stakeholders such as data owners, compliance officers, and information security managers who oversee data protection policies and ensure compliance with regulations.
Compliance Standards
- Cybersecurity is often aligned with cybersecurity frameworks like the National Institute of Standards and Technology (NIST), ISO 27001, and the Center for Internet Security (CIS) Controls. These standards help organizations build robust cybersecurity programs.
- In contrast, information security typically adheres to standards focused on data protection, such as the General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), and Payment Card Industry Data Security Standard (PCI-DSS). These standards are crucial for ensuring data privacy and protection.
Incident Response
- When it comes to incident response, cybersecurity professionals are trained to respond to active cyber attacks and mitigate ongoing threats. Their focus is on immediate defense and damage control during an attack.
- Information security emphasizes the response to data breaches, which includes notification procedures, investigation processes, and remediation of data-related incidents. This ensures that organizations can effectively manage and recover from data breaches.
Perspective
- Lastly, the perspective of cybersecurity is primarily defensive, aiming to protect systems from external threats. Cybersecurity professionals implement measures to fend off attacks and ensure the security of systems.
- In contrast, information security takes a more holistic approach by looking at data security from all angles. This includes not only technical controls but also physical and administrative measures to protect data throughout its lifecycle.
Refer these articles:
- Cyber Security in India: What You Need to Know
- Why Cyber Security Course in India in 2024?
- Cyber Security Scope in India
How Cyber security Is Part of Information Security
Cyber security is not only a critical subset of information security, but also a field with a promising future. As technology advances and businesses increasingly adopt digital infrastructures, the demand for skilled cybersecurity professionals continues to grow. The future in Cyber Security holds significant potential, with opportunities in areas like artificial intelligence-driven security systems, cloud security, and the Internet of Things (IoT) security. Cyber security professionals must stay ahead of evolving threats such as ransomware, advanced persistent threats, and nation-state hacking attempts. By understanding the future in cyber security, organizations can invest in forward-looking strategies and maintain robust defenses against increasingly sophisticated cyberattacks.
Pursuing a Cyber Security certification is an essential step for professionals aiming to enhance their skills and stand out in the industry. Certifications such as Certified Information Systems Security Professional (CISSP), Certified Ethical Hacker (CEH), and CompTIA Security+ validate an individual’s expertise in protecting information systems and responding to security threats. With the growing demand for qualified cybersecurity professionals, earning a Cyber Security certification can boost career prospects and open doors to roles like security analyst, penetration tester, or security consultant. Additionally, these certifications equip professionals with a solid foundation in risk management, cryptography, and incident response, making them valuable assets to organizations.
In today's digital age, acquiring the right Cyber Security skills is crucial for effectively defending against cyber threats. Cyber security skills include knowledge in areas like network security, threat intelligence, vulnerability assessment, and secure software development. Professionals must also develop soft skills such as critical thinking and problem-solving, which are essential for identifying and mitigating security risks. Furthermore, with the growing use of cloud services and IoT devices, cybersecurity professionals need to stay updated on emerging trends and tools to protect against modern-day attacks. By continuously honing their cyber security skills, individuals can stay relevant in a rapidly evolving field, ensuring that organizations can mitigate risks and protect their critical data from breaches.
SKILLOGIC Cyber Security Professional Plus Course offers an exceptional opportunity to build critical skills and advance your career in Cyber Security. Accredited by IIFIS and NASSCOM FutureSkills, the course combines industry-recognized credentials with hands-on experience, real-time projects, and exclusive practice labs. Join a community of over 100,000 learners and secure your future in cyber security with SKILLOGIC Institute.

0
353