Identifying the Role of an Information Security Analyst
An Information Security Analyst is responsible for protecting an organization's systems and data from cyber threats. They assess vulnerabilities, implement security measures, and monitor networks to ensure data integrity and confidentiality.
Ever wondered who keeps our digital secrets safe? Introducing Information Security Analysts, the vigilant protectors of our digital landscape. In this article, we'll uncover their vital role in protecting sensitive information. From assessing risks to responding to threats, learn why their work is essential in keeping our digital lives secure. Let’s explore the realm of cybersecurity together.
What Information Security Analysts Do
According to a report by Markets and Markets, the global information security market is expected to achieve a value of USD 298.5 billion by 2028, with a compound annual growth rate (CAGR) of 9.4% during the forecast period.
In today's digital world, Information Security Analysts are like digital bodyguards. They work to keep important information safe from hackers and cybercriminals. They do this by checking computer systems and networks for any weaknesses that could be exploited. Once they find these weaknesses, they figure out how to fix them and make things more secure.
Imagine if someone could easily access your bank account or personal emails—it would be chaos! That's why information security is super important. It's like putting locks on your doors to keep burglars out. Information Security Analysts help us stay safe by finding and fixing any "digital locks" that might be weak or broken. Without them, our personal information could be at risk of being stolen or misused. So, their job is crucial in making sure our digital lives are safe and secure.
Refer these articles:
- Business Analytics in Supply Chain Management
- Strategic HR Decision-Making Through Business Analytics
- Who is a Business Analyst?
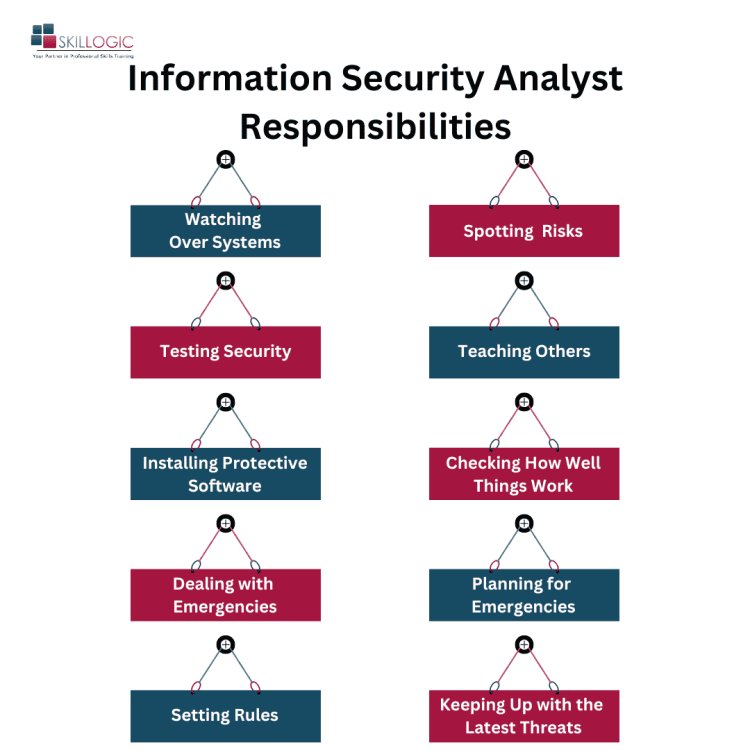
Responsibilities of an Information Security Analyst
An Information Security Analyst plays a crucial role in protecting an organization's information systems from cyber threats. Their responsibilities encompass a wide range of tasks aimed at safeguarding sensitive data and maintaining the integrity of IT systems. Here are the primary responsibilities of an Information Security Analyst:
- Watching Over Systems: They keep a close eye on computers and networks, making sure everything runs smoothly and spotting any odd behavior that might indicate a problem.
- Testing Security: They try to break into their own systems to see if there are any weak spots that hackers could exploit. Then, they figure out how to make things stronger.
- Installing Protective Software: They set up programs that act like digital bodyguards, keeping out viruses, hackers, and other bad stuff.
- Dealing with Emergencies: When there's a security breach, they jump into action, finding out what happened and fixing it as fast as they can to prevent more damage.
- Setting Rules: They create and enforce rules about how information should be kept safe, making sure everyone follows them.
- Spotting Risks: They look for anything that might put information at risk, like outdated software or ways that hackers could get in.
- Teaching Others: They show people in their organization how to stay safe online, like using strong passwords and being careful with suspicious emails.
- Checking How Well Things Work: They regularly check to see if security measures are doing their job properly and if anything needs improving.
- Planning for Emergencies: They make plans for what to do if something goes wrong, so everyone knows what to do in case of a cyberattack or other problem.
- Keeping Up with the Latest Threats: They stay updated on new ways hackers try to break in, so they can stay one step ahead and keep information safe.
Qualifications and Skills Required for an Information Security Analyst
An Information Security Analyst plays a crucial role in protecting an organization's information systems and data from security threats. Here’s a breakdown of the typical qualifications and skills required for this position:
A. Educational Background:
A degree in computer science, information technology, cybersecurity, or a related discipline is typically required. Some employers may also require certifications like Certified Information Systems Security Professional (CISSP) or Certified Ethical Hacker (CEH).
B. Technical Skills:
- Knowledge of Operating Systems: Understanding how operating systems like Windows, Linux, and macOS work is crucial.
- Networking Skills: Knowing how networks operate and being able to troubleshoot network issues.
- Security Tools Proficiency: Familiarity with security tools such as firewalls, antivirus software, and intrusion detection systems.
- Encryption Techniques: Understanding how encryption works to protect data during transmission and storage.
- Programming Skills: Basic programming knowledge in languages like Python, Java, or PowerShell can be beneficial for scripting and automation tasks.
C. Soft Skills:
- Analytical Skills: Being able to analyze complex information and identify potential security risks.
- Problem-Solving Skills: Having the ability to troubleshoot issues and develop effective solutions.
- Communication Skills: The ability to communicate technical information effectively to both technical and non-technical audiences.
- Teamwork: Collaborating effectively with colleagues to address security concerns and implement solutions.
- Attention to Detail: Paying close attention to detail to identify vulnerabilities and ensure thorough security measures are in place.
Having a combination of these educational qualifications and skills is essential for success in the field of information security.
Refer these articles:
- The Future of Business Analytics in 2024
- How to become a Business Analyst in India
- Business Analytics Scope in India
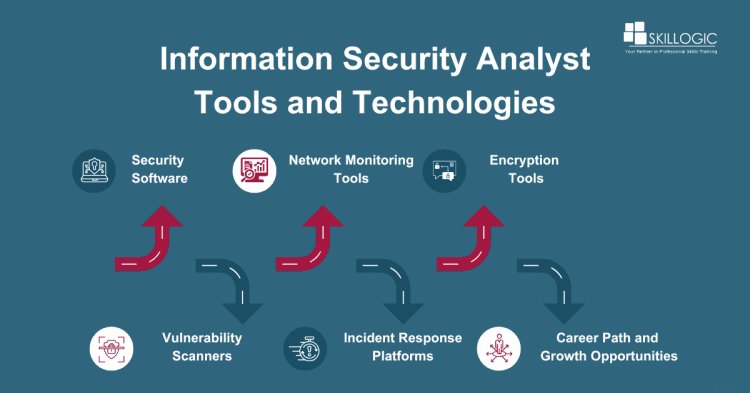
Tools and Technologies Used by Information Security Analyst
Information Security Analysts utilize a variety of tools and technologies to protect an organization's information systems and data. Here’s an overview of some key tools and technologies commonly used in the field:
A. Security Software:
Security software encompasses a range of tools, including antivirus applications, firewalls, and intrusion detection systems (IDS). Antivirus software protects against viruses and malware, while firewalls control network traffic and prevent unauthorized access. IDS tools monitor networks for suspicious activity, alerting analysts to potential threats.
B. Network Monitoring Tools:
Network monitoring tools keep an eye on network traffic, identifying any unusual patterns or behavior that could indicate a security breach. These tools help analysts detect and respond to threats in real-time, ensuring the security of the network.
C. Encryption Tools:
Encryption tools scramble data into a format that can only be read by authorized parties, making it unreadable to anyone else. These tools are crucial for protecting sensitive information during transmission or storage, ensuring confidentiality and integrity.
D. Vulnerability Scanners:
Vulnerability scanners scan systems and networks for weaknesses or vulnerabilities that could be exploited by attackers. By identifying these vulnerabilities, analysts can prioritize patching and fixing them to prevent potential security breaches.
E. Incident Response Platforms:
Incident response platforms help organizations manage and respond to security incidents effectively. They provide workflows and automation to streamline the response process, enabling analysts to contain and mitigate threats quickly to minimize damage and downtime.
Career Path and Growth Opportunities for Information Security Analysts
Information Security Analysts can specialize in various roles, including:
- Security Analyst
- Security Engineer
- Incident Responder
- Penetration Tester
- Security Consultant
A. Entry-Level Positions:
Entry-level positions for Information Security Analysts may include titles such as Junior Security Analyst or Security Administrator. Responsibilities typically involve monitoring systems, assisting with security assessments, and implementing security measures under supervision. These roles provide a foundation for gaining practical experience and understanding the fundamentals of information security.
B. Mid-Level Positions:
Mid-level positions may encompass roles like Security Engineer or Information Security Consultant. Professionals at this level are tasked with designing and implementing security solutions, conducting risk assessments, and managing security incidents independently. They often collaborate with various teams to ensure the organization's security posture is robust and aligned with industry best practices.
C. Senior-Level Positions:
Senior-level positions in Information Security offer leadership opportunities, such as Chief Information Security Officer (CISO) or Security Director. These roles involve strategic planning, policy development, and overseeing the organization's entire security program. Senior Information Security Analysts are responsible for making high-level decisions, managing teams, and ensuring compliance with regulatory requirements.
D. Salary for Information Security Analysts:
- The salary for Information Security Analysts varies depending on factors such as experience, location, and industry.
- In India, the average annual salary for an Information Security Analyst is ₹7,20,000 as reported by Glassdoor.
- In the United States, Cyber Security Analysts earn an average of $1,03,617 per year, according to Glassdoor.
- Payscale reports that the average salary for Information Security Analysts in the United Kingdom is £33,854.
- In Canada, Indeed states that Information Security Analysts earn an average of CAD 88,409 annually.
- Glassdoor indicates that in South Africa, Information Security Analysts earn an average of ZAR 374,000 per year.
- In Australia, the average annual salary for Information Security Analysts is AUD 105,588, according to Indeed.
- Salary Expert notes that Information Security Analysts in Switzerland typically earn around 156,000 CHF annually.
- Indeed reports that in the United Arab Emirates (UAE), Information Security Analysts earn an average of AED 148,118 per year.
- Payscale states that the average salary for Information Security Analysts in Saudi Arabia is SAR 98,400.
- According to Glassdoor, in Germany, Information Security Analysts earn an estimated total pay of €122,524 per year.
Refer these articles:
- Business Analyst Course Fees
- Business Analytics Course Fee in Hyderabad
- Business Analytics Course Fee in Chennai
Why Get an Information Security Certification?
Getting an information security certification can provide numerous benefits, both personally and professionally. Here are some key reasons why pursuing a certification in information security can be advantageous:
- Validation of Skills: Information security certifications validate your knowledge and skills in various areas of cybersecurity, providing employers with tangible evidence of your expertise.
- Career Advancement: Holding certifications can enhance your career prospects by making you more competitive in the job market and opening up opportunities for advancement to higher-level positions.
- Industry Recognition: Information Security Certifications are recognized and respected within the cybersecurity industry, demonstrating your commitment to professionalism and continuous learning.
- Increased Credibility: Having certifications from reputable organizations enhances your credibility as a cybersecurity professional, instilling confidence in employers, clients, and colleagues.
- Specialization: Certifications allow you to specialize in specific areas of cybersecurity such as network security, ethical hacking, digital forensics, or cloud security, enabling you to develop expertise in your chosen field.
- Compliance Requirements: In some cases, certifications may be required to comply with industry regulations or standards, such as PCI DSS, HIPAA, or ISO 27001, making them essential for certain roles or organizations.
The demand for skilled Information Security Analysts is expected to continue growing as organizations increasingly prioritize cybersecurity to mitigate risks, comply with regulations, and make informed data-driven decisions. With continuous advancements in technology, evolving cyber threats, and the integration of business analytics training, careers in information security offer promising opportunities for growth, innovation, and professional development. This blend of cybersecurity and business analytics skills enables professionals to not only protect information systems but also to provide insights that support strategic decision-making.
For professionals aiming to advance their expertise and thrive in Business Analysis, SKILLOGIC Institute is an excellent choice. As a top provider of certification training in PMP, PRINCE2, Six Sigma, DevOps, Cyber Security, and Business Analytics, SKILLOGIC offers accredited programs recognized by IABAC. Our in-depth courses include specialized programs like Business Analytics for Managers, Business Analytics for Marketing, and Business Analytics for HR Professionals. With globally recognized certifications, SKILLOGIC prepares aspiring Business Analysts with the skills and knowledge needed to excel in today's competitive environment.
SKILLOGIC Training Institute offers expert-led certification programs in Six Sigma, PMP, Cybersecurity, and Business Analytics. With over ten years of experience, it delivers practical, career-oriented training. SKILLOGIC has offline centers across major cities in India, making high-quality education easily accessible to help individuals enhance their skills and boost their career progression.

0
223