Ethical Hacking vs Cyber Security: What’s the Difference?

In today’s digital landscape, protecting online information is more essential than ever, given the rising number of cyberattacks. Two major fields that focus on securing our digital world are Cyber Security and ethical hacking, often confused but with distinct roles and objectives. Cyber Security professionals focus on safeguarding systems, networks, and data by implementing security protocols, monitoring for threats, and managing risks, while ethical hackers, or "white-hat hackers," proactively test systems to identify vulnerabilities and prevent potential attacks.
Both fields require specialized skills. Cyber Security experts need proficiency in network security, encryption, and risk management, while ethical hackers must be skilled in penetration testing, vulnerability assessment, and staying updated on hacking techniques. Career opportunities in both fields are abundant. Cyber Security professionals can progress from roles like Security Analyst to senior positions such as Chief Information Security Officer (CISO), with salaries in India ranging from ₹6 to ₹20 lakhs annually, and in the U.S. from $75,000 to $150,000. Ethical hackers can start as penetration testers and move up to roles like Security Consultant, earning between ₹5 to ₹15 lakhs in India and $70,000 to $130,000 in the U.S. Both careers are vital in the fight against cyber threats and offer promising growth and rewards.
What is Cyber security?
Cyber Security refers to the protection of computer systems, networks, and data from unauthorized access, theft, damage, or disruption. It’s about safeguarding information, preventing attacks, and ensuring that systems operate smoothly.
Key Functions of Cyber security
Cyber Security encompasses a wide range of activities designed to protect against cyber threats:
- Prevent unauthorized access: Cyber Security ensures that only authorized users can access sensitive data and systems.
- Maintain data integrity: It ensures that the information remains accurate and untampered with.
- Ensure system availability: Cyber Security professionals work to keep systems running smoothly, even in the event of a cyberattack.
Cyber Security is like a fortress protecting a city. It builds walls, installs alarms, and places guards at the gates to keep out invaders.
Importance of Cyber Security
In an era where almost everything is connected to the internet, from personal devices to national infrastructure, the importance of Cyber Security cannot be overstated:
- Protection against financial loss: A single breach can result in massive financial losses for individuals and companies.
- Safeguarding sensitive information: Personal, corporate, and government data must be protected from hackers.
- Maintaining trust: Customers, employees, and partners trust organizations to keep their information secure. A breach can destroy that trust.
The demand for Cyber Security experts is soaring, with organizations investing heavily in Cyber Security training programs to defend against the latest threats.
Refer these articles:
- Cyber Security for Small Businesses
- Cyber Security Compliance and Regulations
- Zero Trust Architecture: The Future of Cybersecurity
Who is an Ethical Hacker?
An ethical hacker, also known as a "white-hat hacker," uses the same techniques as malicious hackers, but with a positive intent—to strengthen security. Ethical hackers identify vulnerabilities in systems, networks, or applications and report these weaknesses to the organization so they can be resolved before being exploited by cyber criminals. Their goal is to help protect systems from potential attacks by proactively finding and addressing security flaws.
Key Functions of Ethical Hacker
Ethical hackers perform a range of tasks, all focused on identifying weaknesses:
- Penetration testing: This involves simulating cyberattacks to find weak points in a system.
- Vulnerability assessments: Ethical hackers analyze systems for potential vulnerabilities.
- Reporting and remediation: After finding weaknesses, ethical hackers report them to the organization and suggest ways to fix them.
In essence, ethical hackers act like friendly burglars who attempt to break into homes, but only to alert the homeowner to the vulnerability.
Why Ethical Hacking is Crucial
Ethical hacking plays a vital role in maintaining Cyber Security:
- Proactive security measures: Ethical hacking helps organizations identify weaknesses before malicious actors can exploit them.
- Compliance with regulations: Many industries are required by law to perform regular security assessments, often carried out by ethical hackers.
- Continual improvement: As cyber threats evolve, ethical hacking helps companies stay ahead of the curve.
With the rising demand for ethical hackers, many professionals are enrolling in Top Cyber security Institute to specialize in this exciting field.
Refer these articles:
- Cyber Security Scope in India
- Cyber Security in India
- How to Become a Cyber Security Expert in India
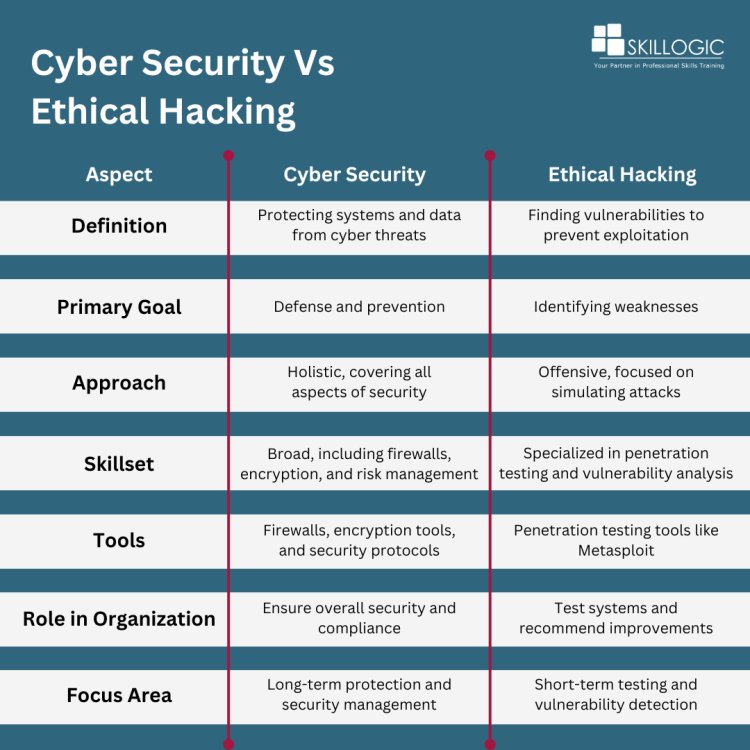
Cyber security vs Ethical Hacking: What’s the Difference?
In today's digital landscape, the importance of safeguarding information and technology cannot be ovsecurityerstated. Two essential fields that contribute significantly to this effort are Cyber Security and Ethical Hacking. While they share a common goal of protecting systems from cyber threats, they approach this goal from different angles. Let’s explore the definitions, primary objectives, methodologies, required skill sets, tools used, roles in organizations, and focus areas of these two critical domains.
Primary Goals
- The primary goal of Cyber Security is defense and prevention. It seeks to establish a secure environment by implementing various strategies and protocols that protect sensitive information from potential threats. Cyber Security professionals work on building robust defenses to ensure that systems remain safe and compliant with regulations.
- In contrast, the primary goal of Ethical Hacking is to identify weaknesses. Ethical hackers aim to uncover vulnerabilities in systems and applications, providing organizations with insights into how they can be exploited. By identifying these weaknesses, they help organizations strengthen their security posture.
Approach
- The approach taken by Cyber Security is holistic. It covers all aspects of security, including risk management, incident response, and compliance with regulations. Cyber Security professionals implement a range of strategies to create a comprehensive security framework that protects an organization from diverse threats.
- Conversely, Ethical Hacking adopts an offensive approach, focusing on simulating attacks to test an organization's defenses. By thinking like a hacker, ethical hackers can identify potential entry points and weaknesses that could be exploited by malicious actors.
Skillset
- When it comes to the skillset, Cyber Security professionals possess a broad range of knowledge and expertise. Their skill set includes firewalls, encryption techniques, risk management, and incident response strategies. They must have a deep understanding of security protocols and the ability to develop comprehensive security policies.
- In contrast, Ethical Hackers have a specialized skill set concentrated in penetration testing and vulnerability analysis. They need to understand various hacking techniques and tools, allowing them to simulate attacks effectively and identify vulnerabilities within systems.
Tools
- The tools used in Cyber security also differ significantly. Cyber Security professionals typically utilize firewalls, encryption tools, and security protocols to establish a secure environment. They focus on preventative measures to safeguard systems from threats.
- Ethical Hackers, however, use penetration testing tools such as Metasploit, Nmap, and Wireshark to conduct their tests. These tools help them identify vulnerabilities, exploit weaknesses, and provide organizations with actionable insights to improve their security.
Role in Organizations
- In an organization, Cyber Security professionals play a critical role in ensuring overall security and compliance. They develop and implement security policies, conduct risk assessments, and respond to incidents, all while maintaining compliance with regulatory standards.
- Ethical hackers, in contrast, concentrate on evaluating systems and providing suggestions for enhancements. They conduct penetration tests and vulnerability assessments to evaluate an organization's security posture, providing valuable feedback on areas that need enhancement.
Focus Area
- Finally, the focus areas of these two fields differ. Cyber Security professionals are primarily concerned with long-term protection and security management. They work on developing a secure infrastructure and maintaining it over time to mitigate risks.
- In contrast, Ethical Hacking has a short-term focus on testing and vulnerability detection. Their work is often project-based, assessing the current state of security and identifying immediate areas for improvement.
In summary, while Cyber Security and Ethical Hacking both aim to protect digital assets, they approach this goal using different methods. A career in Cyber Security centers around developing comprehensive defense systems and long-term security strategies, while Ethical Hacking focuses on uncovering vulnerabilities through simulated attacks. Recognizing these distinctions is crucial for organizations looking to strengthen their security measures and effectively reduce cyber threats.
Refer these articles:
Roles of a Cyber security Expert and an Ethical Hacker
Let’s discuss the critical roles these professionals play in defending against cyber threats, and how their responsibilities complement each other to ensure comprehensive security.
The Role of a Cyber security Expert
A Cyber Security expert is responsible for safeguarding the digital assets of an organization. Their day-to-day activities may include:
- Implementing security protocols: Setting up firewalls, anti-virus software, and encryption techniques to prevent unauthorized access.
- Monitoring networks for threats: Using advanced tools to monitor network traffic and identify potential threats in real-time.
- Training employees: Educating staff about security best practices to reduce the risk of accidental breaches.
Cyber Security experts are the guardians of the digital realm, constantly working behind the scenes to keep hackers at bay. They ensure that the entire organization is protected from the latest threats.
The Role of an Ethical Hacker
An ethical hacker, on the other hand, focuses on probing for weaknesses and testing the limits of security measures. Their responsibilities often include:
- Performing penetration tests: Simulating attacks to find vulnerabilities in a system.
- Reporting findings: Documenting any weaknesses discovered during the tests and suggesting fixes.
- Staying updated on hacking trends: Ethical hackers need to stay ahead of cybercriminals by learning the latest hacking techniques.
While Cyber Security experts defend the digital perimeter, ethical hackers act as the organization’s "attackers," helping identify weak points before real hackers can exploit them.
Both cyber security course and ethical hacking are essential for protecting the digital world. While cyber security focuses on defense, ethical hacking takes an offensive approach to identify weaknesses. Together, they form a robust security strategy, making them both vital career options in today's tech landscape.
At SKILLOGIC Institute, we understand the importance of both ethical hacking and cyber security in today’s digital world. Our Cyber Security Professional Plus Course, accredited by IIFIS and NASSCOM FutureSkills, equips learners with the skills to excel in both areas through real-time projects and hands-on labs. With over 100,000 empowered learners, we focus on practical training and industry-recognized certifications, making us a top choice for those looking to thrive in these crucial fields. Join SKILLOGIC to master both ethical hacking and cyber security and secure the future of digital technology.

0
619